Generate OTP link
Generate OTP Link
Generate an OTP link for passwordless authentication where users click a WhatsApp link to verify their identity.
POST
Generate OTP link
Overview
Generate a magic link for passwordless authentication via WhatsApp. Instead of typing a code, users simply click a pre-formatted WhatsApp link that automatically sends a verification message back to your system. This provides a seamless, user-friendly authentication experience.Quick Demo
How It Works
- Generate an OTP link request with custom messages
- Receive a unique
codeandwhatsapp_link - Send the WhatsApp link to your user (via email, SMS, or your app)
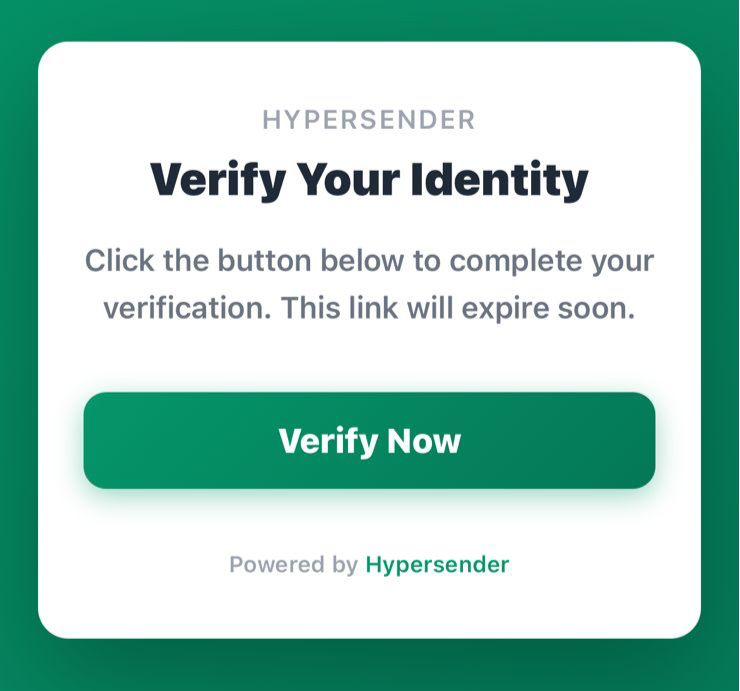
- User clicks the link, which opens WhatsApp with a pre-filled message
- User sends the message (containing the unique code)
- Your system receives the message via webhooks
- User clicks the link and verifies the action
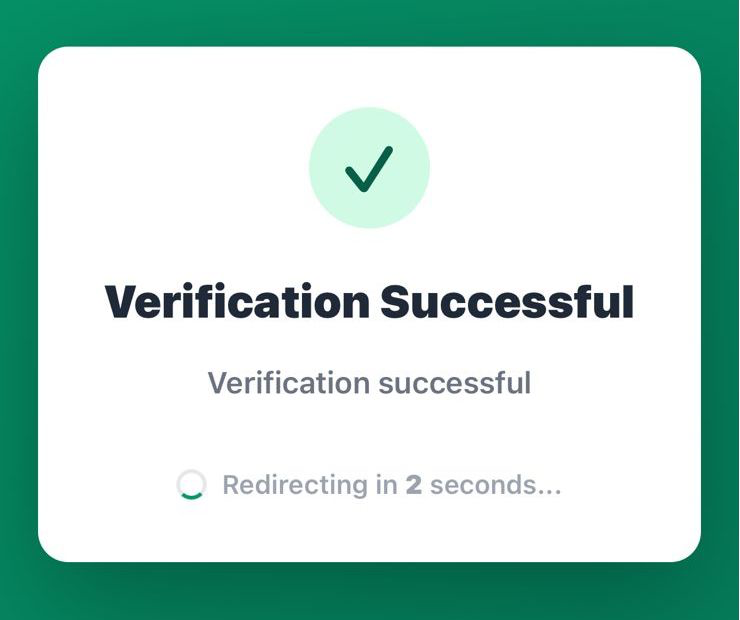
- After verification, the user is redirected to your application with access granted
- Use callbacks to handle success/failure events
Parameters
expires
Time-to-live (TTL) in seconds before the link expires. Default is1800 seconds (30 minutes).
name
Your application or service name to display in messages.message (object)
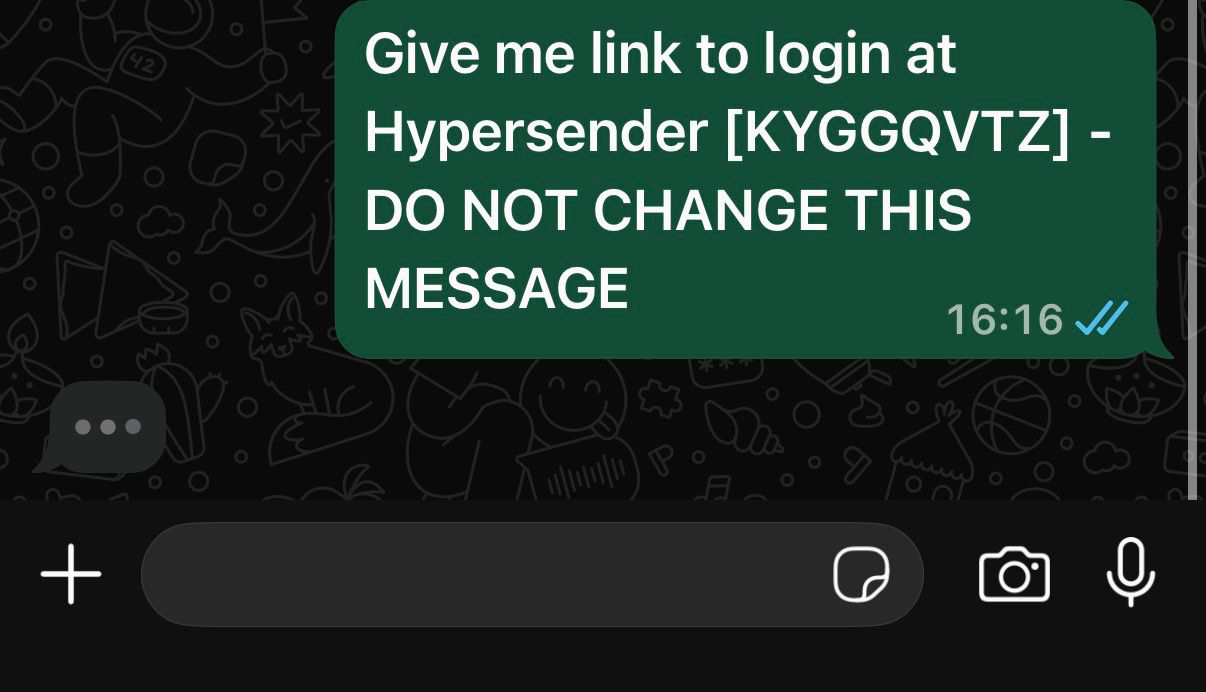
Custom messages for different stages of the verification flow:- prompt: The message users see in the WhatsApp link (e.g., “Give me link to login at MyApp”)
- success: Message sent when verification succeeds. Use
{link}placeholder for the actual login/verification URL - failed: Message sent when verification fails
- expired: Message sent when the link has expired
callback (object)
Webhook URLs to receive verification events:- success: URL called when user successfully verifies
- failed: URL called when verification fails
Response
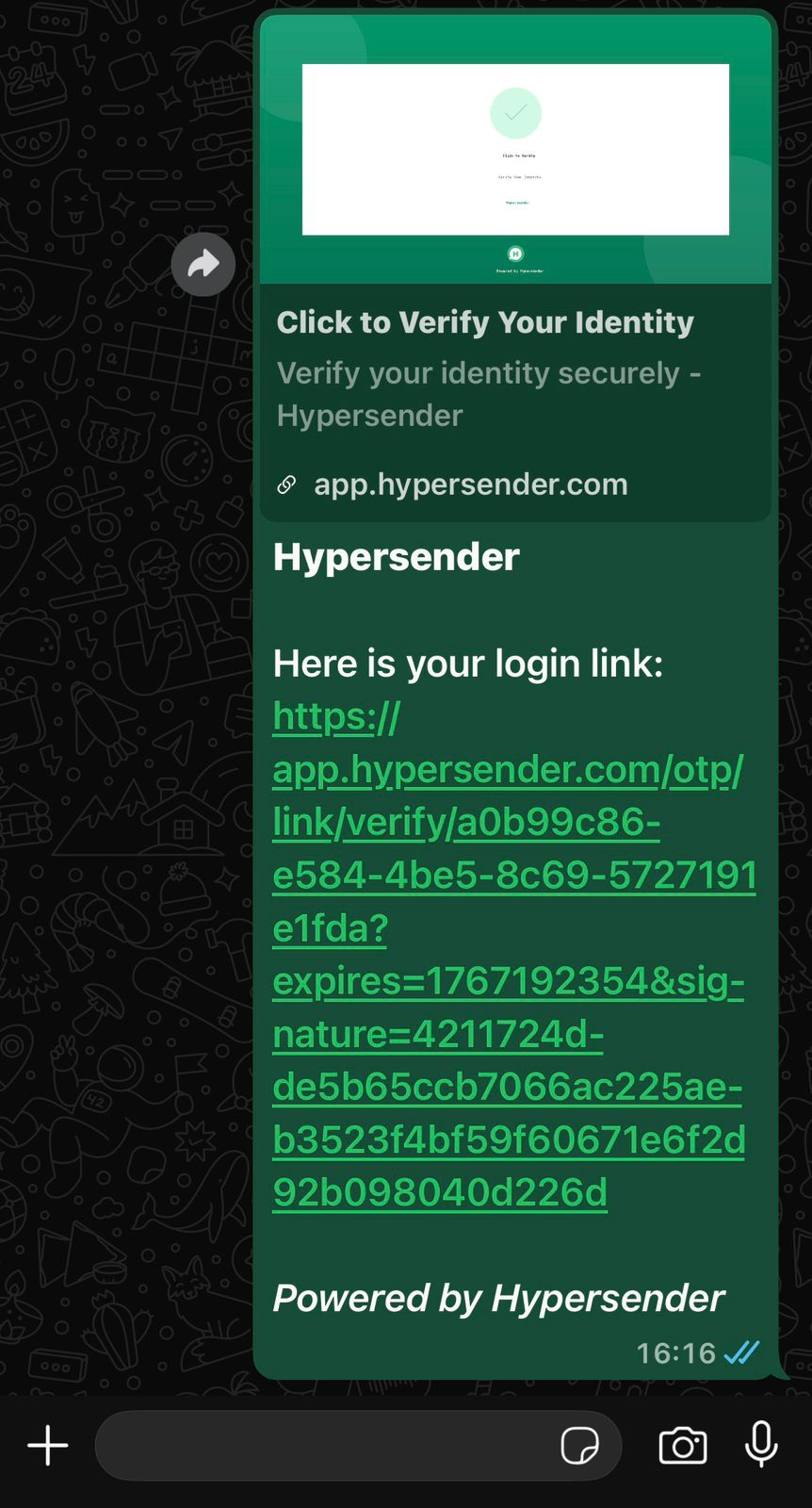
The response includes:uuid: Unique identifier for this OTP link requestcode: Short verification code (e.g., “RDYFQUBX”)chat_id: The recipient’s chat IDstatus: Current status (pending,verified,failed, orexpired)otp_type: Type of OTP (alwayslinkfor this endpoint)expires_at: ISO 8601 timestamp when the link expirescreated_at: ISO 8601 timestamp when the link was createdwhatsapp_link: The complete WhatsApp link to send to the user
The WhatsApp Link
The generatedwhatsapp_link follows this format:
- Pre-fills WhatsApp with the prompt message
- Includes the unique verification code in brackets
- Warns users not to modify the message
Usage Example
Implementation Flow
1. Generate the Link
Call this endpoint to create a verification link for your user.2. Deliver the Link
Send thewhatsapp_link to your user through:
- SMS
- In-app notification
- Web page display
3. User Clicks Link
When clicked, the link:- Opens WhatsApp (mobile) or WhatsApp Web
- Pre-fills a message with the verification code
- User just needs to tap “Send”
4. Handle Callbacks
Your callback URLs will receive POST requests with the verification result:5. Respond to User
Based on the callback, send the appropriate message:- Success: Send the login link or access token
- Failed: Notify user of the error
- Expired: Prompt user to request a new link
Message Placeholders
Use these placeholders in your message templates:{link}: Replaced with the actual authentication/login URL{name}: Your application name{code}: The verification code
Use Cases
- Passwordless Login: Let users log in without typing passwords
- Two-Factor Authentication: Add an extra security layer
- Phone Verification: Verify phone numbers during signup
- Account Recovery: Secure account recovery flow
- Secure Actions: Verify sensitive operations (payments, settings changes)
Security Considerations
- HTTPS Only: Always use HTTPS for callback URLs
- Verify Callbacks: Validate incoming webhook requests
- Short Expiration: Use shorter TTL for sensitive operations
- Rate Limiting: Implement limits on link generation per user
- One-Time Use: Links should be invalidated after use
- Monitor Failed Attempts: Track and alert on suspicious patterns
Monitoring
Track these metrics for security and UX optimization:- Link generation rate
- Click-through rate (users who click the link)
- Verification success rate
- Expiration rate (links that expire unused)
- Failed verification attempts
- Average time to verification
Authorizations
Bearer authentication header of the form Bearer <token>, where <token> is your auth token.
Path Parameters
Hypersender instance UUID